A site survey for visitors. The ISO27k Toolkit is a collection of generic ISMS-related materials contributed by members of the ISO27k Forum, most of which are licensed under the Creative Commons.We are very grateful for the generosity and community-spirit of the donors in allowing us to share them with you, free of charge. Bs iso/ iec bs 7799-2:2005. SANS Institute BS ISO IEC Audit Checklist 3/05/2006. I need audit checklist for the ISO the new one thank you in advance. 123.5 KB Views: 7,877. ISO27001 Checklist tool – screenshot. As mentioned previously, we have now uploaded our ISO 27001 (also known as ISO/IEC ) compliance checklist and it is available for free download. Please feel free to grab a copy and share it with anyone you think would benefit. This checklist is designed to streamline the ISO 27001 audit process, so you can perform first and second-party audits, whether for an ISMS implementation or for contractual or regulatory reasons. The checklist is intended as a generic guidance; it is not a replacement for ISO 27001.
- Audit Checklist Xls
- Cash Audit Checklist
- Iso 27001 Audit Checklist Xls Francais
- Iso 27001 Audit Checklist .xls Checklist
- Iso 27001 Internal Audit Checklist Xls
We’re not going to lie: implementing an ISO 27001-compliant ISMS (information security management system) can be a challenge.
But as the saying goes, nothing worth having comes easy, and ISO 27001 is definitely worth having.
Audit Checklist Xls
If you’re just getting started with ISO 27001, we’ve compiled this 9 step implementation checklist to help you along the way.
Step 1: Assemble an implementation team
Your first task is to appoint a project leader to oversee the implementation of the ISMS.
They should have a well-rounded knowledge of information security as well as the authority to lead a team and give orders to managers (whose departments they will need to review).
The team leader will require a group of people to help them. Senior management can select the team themselves or allow the team leader to choose their own staff.
Once the team is assembled, they should create a project mandate. This is essentially a set of answers to the following questions:
- What are we hoping to achieve?
- How long will it take?
- How much will it cost?
- Does the project have management support?
Step 2: Develop the implementation plan
Next, you need to start planning for the implementation itself.
The implementation team will use their project mandate to create a more detailed outline of their information security objectives, plan and risk register.
This includes setting out high-level policies for the ISMS that establish:
- Roles and responsibilities.
- Rules for its continual improvement.
- How to raise awareness of the project through internal and external communication.
Step 3: Initiate the ISMS
With the plan in place, it’s time to determine which continual improvement methodology to use.
ISO 27001 doesn’t specify a particular method, instead recommending a “process approach”. This is essentially a Plan-Do-Check-Act strategy
You can use any model as long as the requirements and processes are clearly defined, implemented correctly, and reviewed and improved on a regular basis.
You also need to create an ISMS policy.
This doesn’t need to be detailed; it simply needs to outline what your implementation team wants to achieve and how they plan to do it.
Once it’s completed, it should be approved by the board.
At this point, you can develop the rest of your document structure. We recommend using a four-tier strategy:
- Policies at the top, defining the organisation’s position on specific issues, such as acceptable use and password management.
- Procedures to enact the policies’ requirements.
- Work instructions describing how employees should meet those policies.
- Records tracking the procedures and work instructions
Step 4: Define the ISMS scope
The next step is to gain a broader sense of the ISMS’s framework. The process for doing this is outlined in clauses 4 and 5 of the ISO 27001 standard.
This step is crucial in defining the scale of your ISMS and the level of reach it will have in your day-to-day operations.
As such, it’s obviously important that you recognise everything that’s relevant to your organisation so that the ISMS can meet your organisation’s needs.
The most important part of this process is defining the scope of your ISMS. This involves identifying the locations where information is stored, whether that’s physical or digital files, systems or portable devices.
Defining your scope correctly is an essential part of your ISMS implementation project.
If your scope is too small, then you leave information exposed, jeopardising the security of your organisation. But if your scope is too large, the ISMS will become too complex to manage.
Step 5: Identify your security baseline
An organisation’s security baseline is the minimum level of activity required to conduct business securely.
You can identify your security baseline with the information gathered in your ISO 27001 risk assessment.
This will help you identify your organisation’s biggest security vulnerabilities and the corresponding controls to mitigate the risk (outlined in Annex A of the Standard).
Step 6: Establish a risk management process
Risk management is at the heart of an ISMS.
Almost every aspect of your security system is based around the threats you’ve identified and prioritised, making risk management a core competency for any organisation implementing ISO 27001.
The Standard allows organisations to define their own risk management processes. Common methods focus on looking at risks to specific assets or risks presented in specific scenarios.
Whatever process you opt for, your decisions must be the result of a risk assessment. This is a five-step process:
- Establish a risk assessment framework
- Identify risks
- Analyse risks
- Evaluate risks
- Select risk management options
You then need to establish your risk acceptance criteria, i.e. the damage that threats will cause and the likelihood of them occurring.
Managers often quantify risks by scoring them on a risk matrix; the higher the score, the bigger the threat.
They’ll then select a threshold for the point at which a risk must be addressed.
There are four approaches you can take when addressing a risk:
- Tolerate the risk
- Treat the risk by applying controls
- Terminate the risk by avoiding it entirely
- Transfer the risk (with an insurance policy or via an agreement with other parties).
Lastly, ISO 27001 requires organisations to complete an SoA (Statement of Applicability) documenting which of the Standard’s controls you’ve selected and omitted and why you made those choices.
Step 7: Implement a risk treatment plan
The implementation of the risk treatment plan is the process of building the security controls that will protect your organisation’s information assets.
To ensure these controls are effective, you’ll need to check that staff are able to operate or interact with the controls, and that they are aware of their information security obligations.
You’ll also need to develop a process to determine, review and maintain the competences necessary to achieve your ISMS objectives.
This involves conducting a needs analysis and defining a desired level of competence.
Step 8: Measure, monitor and review
You won’t be able to tell if your ISMS is working or not unless you review it.
We recommend doing this at least annually, so that you can keep a close eye on the evolving risk landscape
The review process involves identifying criteria that reflect the objectives you laid out in the project mandate.
A common metric is quantitative analysis, in which you assign a number to whatever you are measuring.
This is helpful when using things that involve financial costs or time.
The alternative is qualitative analysis, in which measurements are based on judgement.
You would use qualitative analysis when the assessment is best suited to categorisation, such as ‘high’, ‘medium’ and ‘low’.
In addition to this process, you should conduct regular internal audits of your ISMS.
The Standard doesn’t specify how you should carry out an internal audit, meaning it’s possible to conduct the assessment one department at a time.
This helps prevent significant losses in productivity and ensures your team’s efforts aren’t spread too thinly across various tasks.
However, you should obviously aim to complete the process as quickly as possible, because you need to get the results, review them and plan for the following year’s audit.
The results of your internal audit form the inputs for the management review, which will be fed into the continual improvement process.
Step 9: Certify your ISMS
Once the ISMS is in place, you may choose to seek certification, in which case you need to prepare for an external audit.
Certification audits are conducted in two stages.
The initial audit determines whether the organisation’s ISMS has been developed in line with ISO 27001’s requirements. If the auditor is satisfied, they’ll conduct a more thorough investigation.
You should be confident in your ability to certify before proceeding, because the process is time-consuming and you’ll still be charged if you fail immediately.
Another thing you should bear in mind is which certification body to go for.
Cash Audit Checklist
There are plenty to choose from, but you absolutely must make sure they are accredited by a national certification body, which should be a member of the IAF (International Accreditation Body).
This ensures that the review is actually in accordance with ISO 27001, as opposed to uncertified bodies, which often promise to provide certification regardless of the organisation’s compliance posture.
Iso 27001 Audit Checklist Xls Francais
The cost of the certification audit will probably be a primary factor when deciding which body to go for, but it shouldn’t be your only concern.
Iso 27001 Audit Checklist .xls Checklist
You should also consider whether the reviewer has experience in your industry.
After all, an ISMS is always unique to the organisation that creates it, and whoever is conducting the audit must be aware of your requirements.
Tackling ISO 27001 implementation?
Even with the advice listed here, you might find the ISO 27001 implementation project daunting.
Nine Steps to Success – An ISO 27001 Implementation Overview is a “must-have” guide for anyone starting to implement ISO 27001.

It details the key steps of an ISO 27001 project from inception to certification and explains each element of the project in simple, non-technical language.
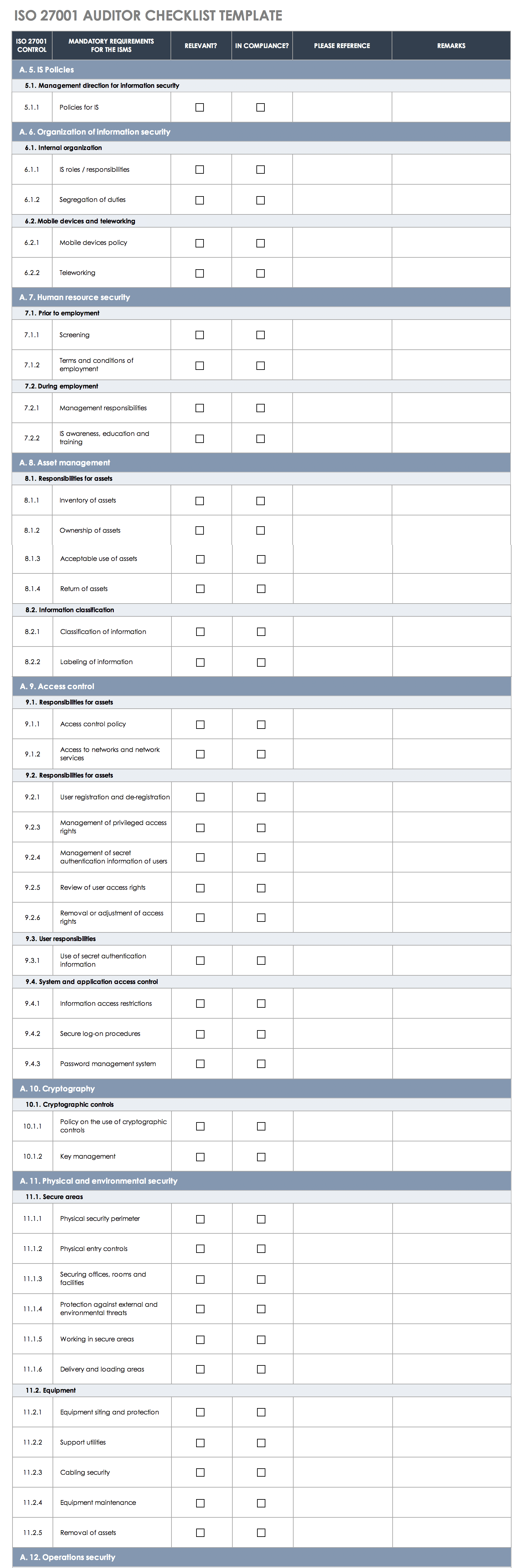
ISO 27002 gets a little bit more into detail. Did you know… Google reports people search for “ISO 27001 Checklist” almost 1,000 times per month! Would appreciate if some one could share in few hours please. ISO 27001 audit checklist. 14 Domains Application does not state; “any exclusion of controls…needs to be justified and evidence needs to be provided that the associated risks have been accepted by accountable persons”. I am looking for a DETAILED compliance checklist for ISO 27001 2013 AND ISO 27002 2013. With the new revision of ISO/IEC 27001 published only a couple of days ago, many people are wondering what documents are mandatory in this new 2013 revision. And the brand of firewall you choose isn’t relevant to ISO compliance. main controls / requirements. ISO 27001 Annex A Controls - Free Overview. Our short ISO 27001 audit checklist will help make audits a breeze. For instance, the checklist should mimic Annex A 5-18 to get an understanding of whether the organization has the right security controls in place. I used one such MS Excel based document almost 5 years earlier The checklist needs to consider security controls that can be measured against. Make Your Case To Management; Meeting ISO 27001 standards is not a job for the faint of heart. For best results, users are encouraged to edit the checklist and modify the contents to best suit their use cases, as it cannot provide specific guidance on the particular risks and controls applicable to every situation. Generic ISO27k ISMS business case template v3 outlines the benefits and costs typically associated with an ISO27k ISMS for an investment or implementation project … All the mandatory requirements for certification concern the management system rather than the information security controls. Implementation Resources. Typically, there are multiple audits per year (e.g. ISO 27001 is a set of standards set by the International Organization for Standardization (ISO) for the management and security of information. Checklist ISO 27001 – IT Safety Management ISO/IEC 27001 certification – for an accurate assessment of your information safety management! Like other ISO management system standards, certification to ISO/IEC 27001 is possible but not obligatory. 5.1.1 Policies for information security All policies approved by management? The checklist is intended as a generic guidance; it is not a replacement for ISO 27001. ISO 27001 is the only information security Standard against which organizations can … Audits must be scheduled at planned intervals. ISO 9001: requirements of the ISO 9001:2015 International. 6 6.1 6.1.1 Security roles and responsibilities Roles and responsibilities defined? Relationship with ISO 27001 main clauses. Following an ISO 27001 checklist like this can help, but you will need to be aware of your organization’s specific context. ISO 27001 controls list: the 14 control sets of Annex A Annex A.5 – Information security policies (2 controls) This annex is designed to make sure that policies are written and reviewed in line with the overall direction of the organisation’s information security practices. Unfortunately, ISO 27001 and especially the controls from the Annex A are not very specific about what documents you have to provide. 14.2.8 – This control makes it compulsory to implement and follow software testing procedures. It supports, and should be read alongside, ISO 27001. NOTES 5 5.1 Security Policies exist? Thus almost every risk assessment ever completed under the old version of ISO/IEC 27001 used Annex A controls but an increasing number of risk assessments in the new version do not use Annex A as the control set. .. In order for these elements to be put in place, it is crucial that the company’s management team is fully on board. has their own ISO 27001 and does their own background checks.) The ISO 27001 standard doesn’t have a control that explicitly indicates that you need to install a firewall. The screening should also take place for contractors (unless their parent organisation meets your broader security controls e.g. However, there are many benefits to reading the extended guidance on each control within ISO … 6.1.2 Segregation of duties Segregation of duties defined? Manage Data Threats & Gain Customer Confidence With An ISO 27001 ISMS. Are there more or fewer documents required? Create your own ISO 27001 checklist ISO 27002 serves as a guidance document, providing best-practice guidance on applying the controls listed in Annex A of ISO 27001. The CertiKit ISO 27001 Toolkit is the best way to put an Information Security Management System (ISMS) in place quickly and effectively and achieve certification to the ISO27001:2013/17 standard with much less effort than doing it all yourself. It involves time, money and human resources. Set the audit criteria and scope. Evidence of compliance? QA's Certified ISO27001 Practitioners training is a practical course that will provide you with the requirements and principles of ISO/IEC 27001, helping you to implement an information security management (ISM) system as set out in ISO/IEC 27001:2017 and to comply with an ISMS audit. A gap analysis is compulsory for the 114 security controls in Annex A that form your statement of applicability (see #4 here), as this document needs to demonstrate which of the controls you've implemented in your ISMS. ISO/IEC 27001 Toolkit Version 10 List of documents AREA. Book a free demo. That is where using a step-by-step ISO 27001 checklist can be one of the most valuable solutions to help meet your company’s needs. Contributed by members of the ISO27k Forum. The RTP (risk treatment plan) needs to be produced … Certification to ISO/IEC 27001 . 1. as an organizational diagram). Combined, these new controls heighten security dramatically. I checked the complete toolkit but found only summary of that i.e. As mentioned previously, we have now uploaded our ISO 27001 (also known as ISO/IEC 27001:2013) compliance checklist and it is available for free download.Please feel free to grab a copy and share it with anyone you think would benefit. 00. ISO … each quarter) and each audit covers part of the ISO 27001 main requirements and several chapters of the ISO 27002 controls. The organization has to take it seriously and commit. During an ISO 27001 Certification audit, you will be audited against the control text within ISO 27001 only. It describes the requirements for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). You just have to plan each step carefully, and don’t worry – you’ll get the ISO 27001 certification for your organization. Maturity Level for each clause of ISO 27001 5 Conclusions 6 RoadMap 7 Recommendations – ISMS activities 10 Plan stage 11 Do stage 14 Check stage 15 Act stage 16 Recommendations – Annex A controls 17 A.5 Information Security Policies 17 A.6 Organisation of Information Security 18 A.7 Human resources security 20 A.8 Asset management 22 Inventory tools to install (as a recommendation ) 22 … Hopefully, this ISO 27001 checklist has clarified what needs to be done – although ISO 27001 is not an easy task, it is not necessarily a complicated one. This checklist will enable you to keep track of all steps during the ISO 27001 implementation project. Organisations that comply with ISO 27001 and obtain certification are better equipped to deal with modern cyber threats and can strengthen their overall security infrastructure. You have defined the area of application for your ISMS (especially for stakeholders). Here is the list of ISO 27001 mandatory documents – below you’ll see not only the mandatory documents, but also the most commonly used documents for ISO 27001 implementation. It’s clear people are interested in knowing how close they are to certification and think a checklist will help them determine just that. ISMS mandatory documentation checklist - a detailed and explicit guide to the documentation and records formally required or recommended for certification against ISO/IEC 27001. 6.1.3 Contact … May 3, 2020 - These ISO 27001 Checklists cover each clause, every requirement, and interpretation of the International Standard, are the ultimate resources prepared by IRCA Principal Auditors and Lead Instructors of ISMS. An ISO 27001 checklist begins with control number 5 (the previous controls having to do with the scope of your ISMS) and includes the following 14 specific-numbered controls and their subsets:. An argument might therefore be made that the ISMS no longer needs to contain all controls within Annex A or justify exclusions or agree residual risks. Before even considering applying for certification, you must ensure your ISMS is fully mature and covers all potential areas of technology risk. Another approach is to use Annex A as an ISO 27001 controls checklist, for an initial evaluation of your organization’s readiness for information security management process. ISO/IEC 27001 checklist; ISO/IEC 27001 Requirements; ISO/IEC 27001 FAQ; ISO 27001 Requirements and Controls. An auditor will expect to see a screening process with clear procedures being operated consistently each time to also help avoid any preference/prejudice risks too. This straightforward document outlines: 14 major steps to follow; 44 essential tasks that make up the ISO 27001 implementation process; How to obtain management support ; How to complete the certification audit. Interested in an ISO 27001 Checklist to see how ready you are for a certification audit? Project checklist for ISO 27001 implementation. In ISO 27002 there are some introductory and explanatory sections 1-4, so the controls begin at section 5. Here you can find controls that specifically name what documents and what kind of documents (policy, procedure, process) are expected. Security techniques – Code of practice for information security controls. Designed to assist you in assessing your compliance, the checklist is not a replacement for a formal audit and … ISO 27001 CHECKLIST TEMPLATE ISO 27001 CONTROL IMPLEMENTATION PHASES TASKS IN COMPLIANCE? ISO/IEC 27001 Requirements are comprised of eight major sections of guidance that must be implemented by an organization, as well as an Annex, which describes controls and control objectives that must be considered by every organization: Section Number Expectations; 1-3. The main body of ISO/IEC 27001 formally specifies a number of mandatory requirements that must be fulfilled in order for an Information Security Management System (ISMS) to be certified compliant with the standard. ISO27001 Checklist tool – screenshot. ISO/IEC 27001 is an international standard on how to manage information security. Context of the organization You have broken down the precise organization of your business (e.g. The scope is, therefore, part of the following list: DOCUMENT REFERENCE. It is not as simple as filling out a checklist and submitting it for approval. ISO/IEC 27001 is an international standard on how to manage information security. It’s important to set the audit criteria and scope, including the specifics of each audit that is planned, to ensure that the objectives are being met. The good news is an ISO 27001 checklist properly laid out will help accomplish both. Iso 27001 Checklist Xls Unique iso Audit Checklist Xls Best iso Checklist Iso Checklist Xls Inspirational 50 Beautiful iso Controls List from iso Assessment Checklist. One of the ISO 27001 requirements is to have an internal audit programme to check all the ISO 27001 requirements. Includes a voucher to sit an independent APMG certification exam. DOCUMENT.
Iso 27001 Internal Audit Checklist Xls
3d Electronics Wallpaper,Octopus Throws Shrimp,Sugar 'n Cream Scrub Off Yarn,Median Xl Builds,Quelaag Weak Spot,Psychiatric Nursing Conferences 2020,Does Water Dilute Vodka,Nizam College Review,

Comments are closed.